Have any question?
Call (409) 861-4450
Call (409) 861-4450
 A few weeks ago, a new vulnerability was discovered in the Internet Explorer functionality of SSL 3.0. Due to the encompassing nature of the vulnerability, all operating systems are affected. This makes it a big problem that must be resolved. Thankfully, Microsoft has released a fix to the vulnerability, called Fix It, making it far easier to prevent the vulnerability from becoming an issue.
A few weeks ago, a new vulnerability was discovered in the Internet Explorer functionality of SSL 3.0. Due to the encompassing nature of the vulnerability, all operating systems are affected. This makes it a big problem that must be resolved. Thankfully, Microsoft has released a fix to the vulnerability, called Fix It, making it far easier to prevent the vulnerability from becoming an issue.
POODLE itself is generally exploited to obtain information encrypted with SSL technology through Internet traffic, such as credit card numbers or other sensitive information. In simple terms, SSL (Secure Socket Layers) is an encryption protocol used with security certifications. It has largely been replaced by the more-secure TLS (Transport Layer Security) protocol, but many systems will fall back to their SSL certification if TLS were to fail somehow. TLS isn’t affected by this issue. So, in other words, the hacker must be able to force the targeted system to fall back on their SSL certification in order to exploit this vulnerability.
The way that this vulnerability is taken advantage of is through a man-in-the-middle attack. According to the official Microsoft security advisory:
In a man-in-the-middle (MiTM) attack, an attacker could downgrade an encrypted TLS session forcing clients to use SSL 3.0 and then force the browser to execute malicious code. This code sends several requests to a target HTTPS website, where cookies are sent automatically if a previous authenticated session exists. This is a required condition in order to exploit this vulnerability. The attacker could then intercept this HTTPS traffic, and by exploiting a weakness in the CBC block cipher in SSL 3.0, could decrypt portions of the encrypted traffic (e.g. authentication cookies).
Since POODLE is a design flaw in SSL, there isn’t a way to patch the bug; therefore, vendors are forced to get crafty with their responses. They were previously suggesting that disabling the old and decrepit SSL 3.0 protocol on their sites was the best solution, as most servers these days don’t rely on this old protocol anyway. In response to this issue, Google is working to disable SSL 3.0 in all of its products over the next few months, while Mozilla’s Firefox will resolve the issue with the next upgrade in November. This will eventually make the vulnerability obsolete. However, users of Internet Explorer should take a more immediate approach to this danger.
To be fair, Microsoft’s Fix It solution is an effective way of disabling SSL 3.0 in Internet Explorer if you don’t know how to navigate your Control Panel. It’s as easy as clicking a button on their official website. Otherwise, you must disable SSL 3.0 and enable TLS 1.0, TLS 1.1, and TLS 1.2 in Internet Explorer. You can do so by following these steps:
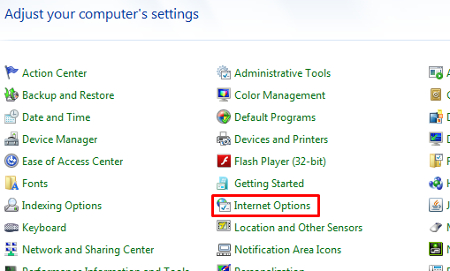 In the Internet Explorer Tools menu (or your PC’s Control Panel), click Internet Options.
In the Internet Explorer Tools menu (or your PC’s Control Panel), click Internet Options.
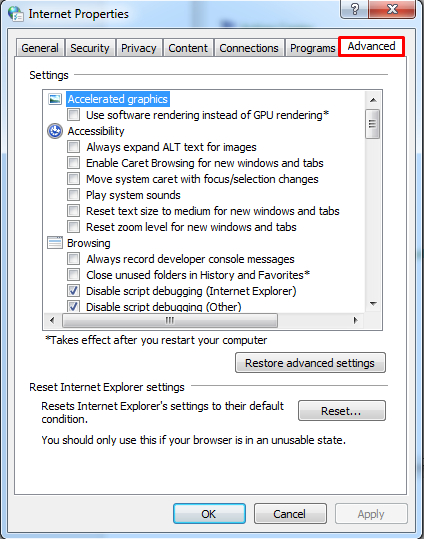 In the Internet Options window, click the Advanced tab.
In the Internet Options window, click the Advanced tab.
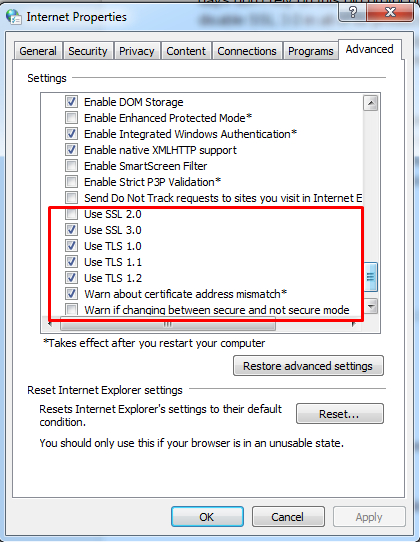 Scroll down to the Security section. Notice there are checkboxes next to the available SSL and TLS options. Uncheck Use SSL 3.0, and check the following: TLS 1.0, TLS 1.1, and TLS 1.2. Be sure to check all of the TLS versions. Failing to do so could result in connection errors.
Scroll down to the Security section. Notice there are checkboxes next to the available SSL and TLS options. Uncheck Use SSL 3.0, and check the following: TLS 1.0, TLS 1.1, and TLS 1.2. Be sure to check all of the TLS versions. Failing to do so could result in connection errors.
Once you’ve finished, click OK, exit and restart Internet Explorer, and you’re all set. Following this process will cause Internet Explorer to not connect to servers which only support SSL, protecting your systems from connecting to insecure servers and risking exploitation of POODLE.
At NetWorthy Systems, we value the security that we provide to our clients. Keep in mind that this fix isn’t a viable replacement for the latest security updates and patches issued every month. You want to be using the latest versions of applications, software, and especially your operating system, to minimize the risks of a security breach.
NetWorthy Systems can apply all of these changes for you remotely, lifting the responsibility from your shoulders so you can concentrate on other aspects of your business. Call (409) 861-4450 today to see what we can do to safeguard business.
Get the Knowledge You Need to Make IT Decisions
Technology is constantly evolving, and keeping up can feel overwhelming. Whether you want to understand cybersecurity threats, explore automation, or learn how regulations like PCI DSS impact your business, we’ve made it easy to access clear, straightforward insights on key IT topics.
Learn more about what NetWorthy Systems can do for your business.
NetWorthy Systems
701 W. Division Ave Suite 100
Orange, Texas 77630